SSL 协议建立过程
来源:互联网 发布:csi网络犯罪调查 编辑:程序博客网 时间:2024/04/25 10:14
Secret Key Cryptography (私密密钥)对称密钥
A B 必须事先知道私密密钥,双方用相同的key来通讯。私密密钥分发不方便,不同的通讯双方要用不同的密钥,否则第
三方就可以监听和中间人攻击
Public Key Cryptography 公开密钥 不对称密钥
A的公钥大家都可以得到,私钥只有A有。发起方B用A的公钥加密数据发送给A,A用私钥解密后再用私钥加密发回B。B看数
据对就知道确实跟A通讯。公开密钥很好的解决了双方认证问题,但仍然无法解决数据被偷窥的问题。因为A的公钥是公开的
,只要得到A发出的密文就可以知道A发送的信息。
对称密钥的有点是速度快,缺点是分发不容易,非对称密钥的有点是分发容易,速度慢。SSL利用非对称密钥来分发对称密钥,最后使用对称密钥来解决通信安全问题。同时通过引入CA来解决中间人攻击!
sun 的 JSSE 参考文档
http://download.oracle.com/javase/6/docs/technotes/guides/security/jsse/JSSERefGuide.html
The SSL Protocol
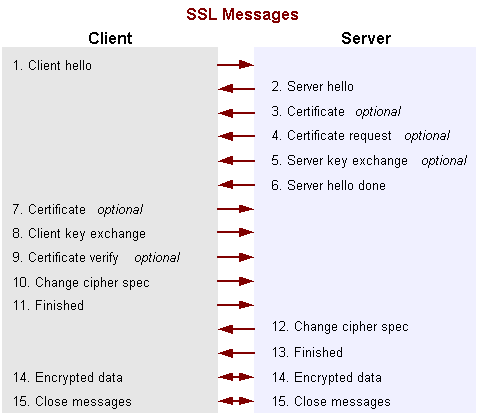
The SSL messages are sent in the following order:
- Client hello - The client sends the server information including the highest version of SSL it supports and a list of the cipher suites it supports. (TLS 1.0 is indicated as SSL 3.1.) The cipher suite information includes cryptographic algorithms and key sizes.
- Server hello - The server chooses the highest version of SSL and the best cipher suite that both the client and server support and sends this information to the client.
- Certificate - The server sends the client a certificate or a certificate chain. A certificate chain typically begins with the server's public key certificate and ends with the certificate authority's root certificate. This message is optional, but is used whenever server authentication is required.
- Certificate request - If the server needs to authenticate the client, it sends the client a certificate request. In Internet applications, this message is rarely sent.
- Server key exchange - The server sends the client a server key exchange message when the public key information sent in 3) above is not sufficient for key exchange.
- Server hello done - The server tells the client that it is finished with its initial negotiation messages.
- Certificate - If the server requests a certificate from the client in Message 4, the client sends its certificate chain, just as the server did in Message 3.
Note: Only a few Internet server applications ask for a certificate from the client.
- Client key exchange - The client generates information used to create a key to use for symmetric encryption. For RSA, the client then encrypts this key information with the server's public key and sends it to the server.
- Certificate verify - This message is sent when a client presents a certificate as above. Its purpose is to allow the server to complete the process of authenticating the client. When this message is used, the client sends information that it digitally signs using a cryptographic hash function. When the server decrypts this information with the client's public key, the server is able to authenticate the client.
- Change cipher spec - The client sends a message telling the server to change to encrypted mode.
- Finished - The client tells the server that it is ready for secure data communication to begin.
- Change cipher spec - The server sends a message telling the client to change to encrypted mode.
- Finished - The server tells the client that it is ready for secure data communication to begin. This is the end of the SSL handshake.
- Encrypted data - The client and the server communicate using the symmetric encryption algorithm and the cryptographic hash function negotiated in Messages 1 and 2, and using the secret key that the client sent to the server in Message 8.
Close Messages - At the end of the connection, each side will send a close_notify message to inform the peer that the connection is closed.
If the parameters generated during an SSL session are saved, these parameters can sometimes be re-used for future SSL sessions. Saving SSL session parameters allows encrypted communication to begin much more quickly.



