LESSON 5 SYSTEM IDENTIFICATION part VI
来源:互联网 发布:算法初步高考题附答案 编辑:程序博客网 时间:2024/04/29 21:29
Exercises:
Run netstat on your local computer, using the -a switch.
netstat -a
What ports are open? Using a web search engine, can you match these ports with the
services that run on them? (This would be a good exercise to try at home, also, to see if your
computer is running unnecessary – and potentially dangerous – services, such as FTP and
telnet.)
Run nmap, using the -sS (for SYN Stealth scan), and -O (for guess operating system) switches
and the IP address 127.0.0.1 as the target.
nmap -sS -O 127.0.0.1
The IP address 127.0.0.1 specifies the local host, or your local computer. (Note: this is different
from the IP address that other computers on the internet use to communicate with yours; on
any machine, the IP address 127.0.0.1 refers to the local computer) What open ports does
nmap find? What services and programs are using these ports? Try running nmap while you
have a web browser or telnet client open. Does this change the results?
练习:
在电脑上运行netstat命令,加上-a:
netstat -a
打开的接口有哪些?使用搜索引擎,查找这些端口和哪些服务相关?(这是个可以在家好好练习的练习题,可以检查
你的电脑上有没有运行一些没必要的,存在潜在安全问题的程序,例如FTP和远程登录。)
运行nmap,使用-sS(扫描同步环线隐身),和-O(猜测操作系统)命令,操作目标的IP地址是127.0.0.1。
nmap -sS -O 127.0.0.1
127.0.0.1是本地计算机的IP地址,即你的电脑。(注意:这个IP地址和网络中别人和你电脑交流时你电脑所用的IP地址不同,
在任何机子上,127.0.0.1都表示本地计算机)nmap发现了哪些开放的接口?使用这些接口的服务和程序是哪些?在打开一个
网络浏览器或者远程登录客服端的时候运行nmap。结果和上面有什么不同?
5.3 System Fingerprinting
Now that you know how to identify a server and how to scan for open ports and use this
information to determine what services are running, you can put this information together to
fingerprint a remote system, establishing the most likely operating system and services that the
remote computer is running.
5.3 指纹识别系统
现在你知道如何识别一台服务器,以及如何查看开放接口,并通过这些信息判断正在运行的服务器,你可以将这些信息集合在
一起来识别一个远程系统,确定在远程电脑上最可能运行的操作系统和服务器。
5.3.1 Scanning Remote Computers
Using an IP address or a domain name other than 127.0.0.1 as an argument for nmap allows
you to scan for open ports on remote computers. It doesn't mean that there will be open
ports, or that you will find them, but it does allow you to try.
For example, imagine that you have been receiving a large amount of spam e-mails, and you
want to discover information about the person who is sending you these e-mails. Looking at
the headers of one of the e-mails, you see that many of the e-mails have originated from the
same IP address: 256.92.116.13 (see Lesson 9: E-mail Security for more details on reading email
headers).
A whois lookup shows you that the address is part of a block assigned to a large ISP, but gives
you no information regarding this particular IP address.
5.3.1 查看远程电脑
用不同于127.0.0.1的IP地址和域名作为nmap的依据,可以查看远程电脑上开放的端口。这不是说那台电脑上有开放
的端口或者你能查看到这些开放端口的信息,但是你可以通过这种方法来试试。
例如,假如你接收到大量的垃圾邮件,你想查出给你发送这些垃圾邮件的人的信息。首先查看其中一封邮件的标题,你会发现
许多的这种邮件来自一个相同的IP地址:256.92.116.13 (查看第9节:通过查看邮件的标题知道关于邮件安全的更多细节)。
通过一个域名查询器你可以知道这个地址是一个大的网络服务提供商提供的分程序的一部分,但不会给你提供关于这个IP地址
的其它任何信息。
If you then use nmap to scan the computer at that address, you get the following results:
nmap -sS -O 256.92.116.13
如果你用nmap查看这个IP地址的电脑,你会得到如下结果:
nmap -sS -O 256.92.116.13
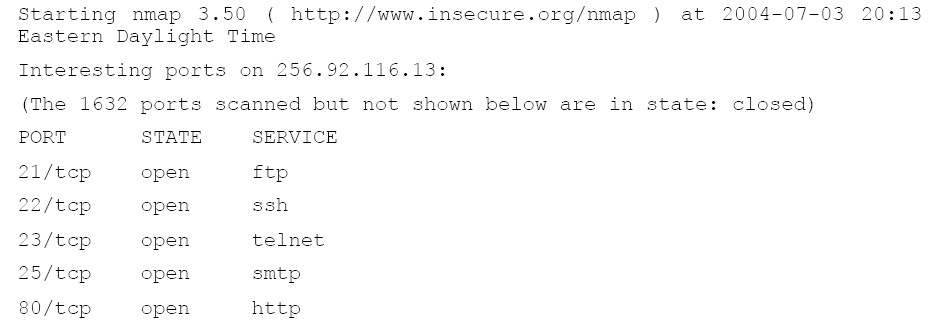
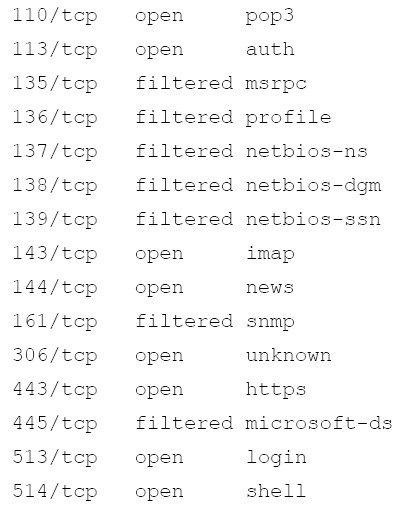
The ports marked as filtered are well-known as potentially vulnerable to attack, so it is not a
surprise to find them listed as filtered. What is most interesting is that ports 21, 22 and 23 – for
ftp, ssh and telnet – are all listed as open.
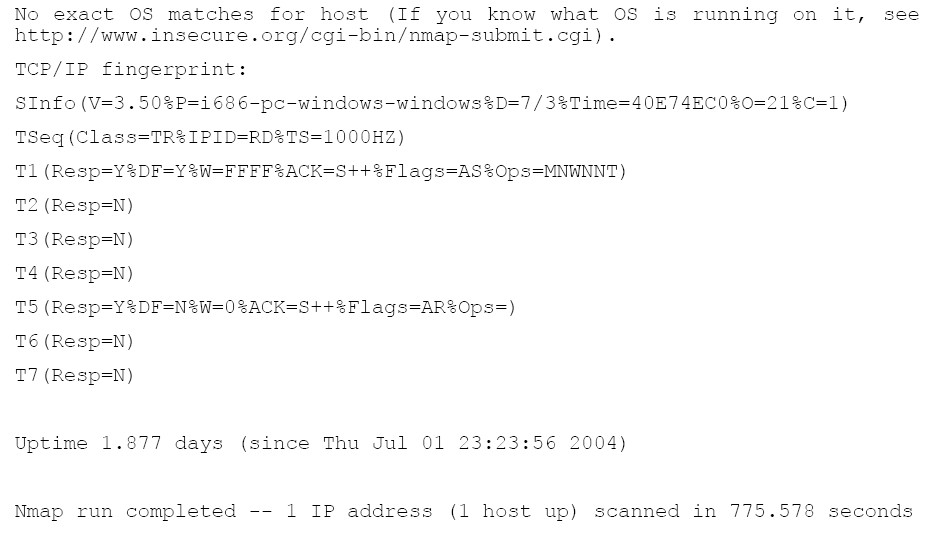
The last thing that nmap does is to try to identify the operating system that is running on the
scanned computer. In this instance, the tests that nmap runs are inconclusive, however, since
nmap does show that ftp and telnet services are both running, you can attempt to connect
through each of those to see if there is a banner that will be broadcast.
被标记不开放的接口(不太懂是什么意思)是潜在攻击的弱点,所以他们会被列为不开放的。很有趣的现象是接口21,22
和23-与ftp,ssh和telnet对应-列为开放。
nmap做的最后一件事是尝试识别在远程电脑上运行的操作系统。在这种情况下,nmap运行的测试是不确定的,但是,
因为nmap显示ftp和telnet服务在运行,你可以尝试通过接这两个服务来连接远程电脑查看是否有信息将被广播。
When you connect through FTP you see a banner that says:
220 ftp316.pair.com NcFTPd Server (licensed copy) ready.
When you then connect through telnet, the computer displays a banner which says
FreeBSD/i386 (ttyp7)
A quick web search tells you that NcFTPd is a Unix program and that FreeBSD is a Unix-type
operating system, so it is likely that the server is running a version of FreeBSD as its operating
system. You can't be certain that this is accurate (banners can be spoofed), but you can
accept this as a reasonable guess.
So, by using nmap, along with FTP and telnet, you have determined that the server which has
been sending you spam runs a Unix-type operating system – probably FreeBSD – and is set up
to send and receive a large variety of information, through a number of services including FTP,
telnet, http, smtp and pop3.
当你通过FTP连接时,你看到一条如下的标语:
220 ftp316.pair.com NcFTPd Server (licensed copy) ready.
当你通过telnet连接时,电脑会展示一个标语:
FreeBSD/i386 (ttyp7)
通过上网查询你会知道NcFTPd 是一个Unix程序,FreeBSD 是一个Unix型的操作系统,所以很有可能该服务器正在
运行FreeBSD版本的操作系统。你不能肯定这是否准确(标语可能是骗人的),但是你可以这么假定。
所以,通过nmap和FTP,telnet,你可以确定向你发送垃圾邮件的服务器运行一个Unix型的操作系统-可能是FreeBSD-
并且通过很多的服务包括FTP,telnet,http,smtp和pop3来发送和接受大量的信息。
Further Reading(深入阅读)
Nmap: http://www.insecure.org/nmap/ (Nmap)
More on Nmap:(更多关于Nmap知识的网站)
http://www.networkmagazine.com/shared/article/showArticle.jhtml?articleId=8702942&classr
oom=
Fport:http://www.foundstone.com/index.htm?subnav=resources/navigation.htm&subcontent
=/resources/proddesc/fport.htm
A number of site detailing ports and the services that use them:(通过下列网站了解接口和使用这些接口的服务)
http://www.chebucto.ns.ca/~rakerman/port-table.html
http://www.chebucto.ns.ca/~rakerman/port-table.html#IANA
http://www.iana.org/assignments/port-numbers
http://www.networksorcery.com/enp/protocol/ip/ports00000.htm
Various DNS lookups: http://www.dnsstuff.com/(域名查询器)
Ping:http://www.freesoft.org/CIE/Topics/53.htm
- LESSON 5 SYSTEM IDENTIFICATION part VI
- LESSON 5 SYSTEM IDENTIFICATION part I
- LESSON 5 SYSTEM IDENTIFICATION part II
- LESSON 5 SYSTEM IDENTIFICATION part III
- LESSON 3 PORTS AND PROTOCOLS part VI
- LESSON 4 SERVICES AND CONNECTIONS part VI
- LESSON 7 ATTACK ANALYSIS part VI
- LESSON 8 DIGITAL FORENSICS part VI
- LESSON 9 E-MAIL SECURITY part VI
- 系统辨识 system identification
- LESSON 1 -part 1
- LESSON 1 -part 2
- LESSON 1 -part 3
- LESSON 1 -part 4
- LESSON 1 -part 1 answer
- LESSON 1 -part 2 answers
- LESSON 1 -part 3 answer
- LESSON 1 -part 4 answers
- ThreadPool
- C++之虚拟析构函数
- C语言宏定义技巧(常用宏定义)
- 数据库分页语句使用
- 注意sizeof 返回值类型
- LESSON 5 SYSTEM IDENTIFICATION part VI
- 设计模式
- VC 预编译头的使用
- 套接口和标准io
- 如何用vlookup求两个表交集
- 虚构函数不是虚函数的话,可能有什么影响。
- 如何通过控制端口保障电脑安全(黑客技术小应用)
- 文本文件与二进制文件的编码差别
- 系出名门Android(2) - 布局(Layout)和菜单(Menu)


