How to View / Disconnect Remote Desktop Sessions from Commandline
来源:互联网 发布:短线长线知乎 编辑:程序博客网 时间:2024/04/28 15:14
Original Post can be found here:http://www.techtalkz.com/blog/tips-n-tricks/how-to-view-disconnect-remote-desktop-sessions-from-commandline.html
I used to receive the maximum number of connections error message when I try to log on to the Windows 2003 Server in my office viaWindows Remote Desktop.
“The terminal server has exceeded the maximum number of allowed connections“

This is pretty annoying if you have some urgent work to do in the server. Most of the already logged in users won’t even be using the session at the time, but I can’t login! So how to solve this? After a bit of googling, as usual, I found a simple way to disconnect other remotely logged in sessions. ![]()
First of all you must be logged in to your client computer as a domain Admin user. Now open the command prompt and type in the following command.
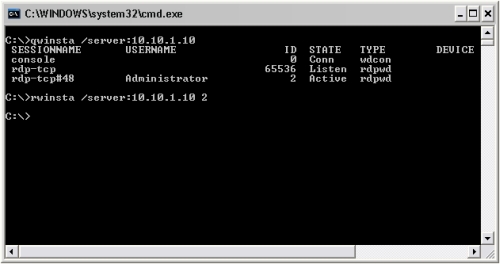
qwinsta /server:SERVERIP
The Ip address or domain name of the Remote server should be entered in place of SERVERIP
Example:
qwinsta /server:10.10.1.10
You will get a list of the Remote Sessions in the command window.

In the above sceenshot we can clearly see an Active RDP session with the ID 2 which belongs to the user Administrator. In order to disconnect that user we are going to use the session ID. Use the following command line to disconnect the remote session.
rwinsta /server:SERVERIP SESSIONID
For example in order to terminate the session of the Administrator user the following command should be given.
rwinsta /server:10.10.1.10 2
Now let’s confirm if the user is really disconnected. Just type in the qwinsta command in proper format.

As you can see our session with ID 2 is no longer there. Now for the user we just disconnected will see the following message.
The remote session was disconnected because you session was logged off at the remote computer. Your administrator or another user might have ended your connection.
So we are done with the remote session management over command lines.
Troubleshooting: How do I solve the "access denied" error?
Referenced from: http://communities.quest.com/docs/DOC-11895
This section describes the solution for the “access denied” error occurs when using qwinsta.exe/rwinsta.exe or WTSOpenServer Windows API function to access to a Windows XP SP2 PC (to read the original article go tohttp://www.codesoil.net/2007/08/16/big-problem-access-denied-when-using-qwinstaexe-or-wtsopenserver-api/).
The same thing happens when you are trying to connect to a Windows XP SP2 using Terminal Services Manager from a Windows 2003 Server.
- Because essentially qwinsta.exe command calls WTS functions (WTSOpenServer, WTSEnumerateSessions, …), you will encounter the same error when using either the command or the API.
As a quick answer, check the following points.
1. Ensure you have the correct credential
Although you do not need to provide a username and a password when executing qwinsta.exe or WTSOpenServer, Windows use its stored credentials automatically, just like accessing a shared folder.
The easiest way to confirm the credential is to use Explorer to access remote server’s C$ share. Also, you can use “net use” command.
For those who want to connect to a remote server programmatically using WTSOpenServer API, WNetAddConnection2 function should be enough to make sure you got a piece of credential before calling WTSOpenServer function.
Of course the user in the credential should be a use on the remote server who has enough privilege to carry out the operation.
2. Open RPC ports on firewall
An API call involves connecting to a remote machine use RPC. In most cases the RPC service is running and you can confirm that from the service management interface. To open RPC ports, simply enable “File and Printer Sharing” in the Windows Firewall setting.
(Generally, if the RPC is blocked by the firewall on remote machine, the error should be "1722 RPC server is unavailable" rather then "5 Access denied")
3. Disable "Force Guest" log on
You can change this option from either local security policy or registry.
Local security policy : run secpol.msc > Secuirty Settings > Local Policies > Security Options > Network access : Sharing and security model for local accounts, and set to "Classic".
Registry : find "forceguest" item in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa, and set it to 0.
The two ways are equivalent. If this option is set to 1, remote logged in user will be impersonated as Guest account (and if Guest account is disabled, login fails). Set it to 0 enables user logging in as themselves.
4. If you still receive “access denied” and it only happens when the remote OS is Windows XP SP2, it is very probably the following case
To confirm, you need a packet sniffer such as Wireshark (a great freeware).
When you use a sniffer to capture the SMB packets, you can see the authentication is OK (NTLM if workstation, Kerberos if Windows 2003 domain), but the RPC get nca_s_fault_access_denied (0×00000005) as error code.
This means the remote RPC component failed to execute the requested operation. It is because in Windows XP SP2, it is not allowed to operate on terminal service (Remote Desktop) through RPC by default. To modify this setting to enable Remote Desktop API through RPC, you need to find the following registry key:
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server
Then add a DWORD value named “AllowRemoteRPC” and change its value to 1.
I googled it and it seems there is no official document on it. (I don’t know why).
Access denied error often misleads us into thinking it must be because of the insufficient privilege, or because that the qwinsta.exe command / WTSOpenServer failed to utilized the credential. It wasted me about 5 hours in researching how to attach a credential to a RPC call, and I even got caught deeply into the complicated SSPI/LSA authentication architecture.
- How to View / Disconnect Remote Desktop Sessions from Commandline
- How To Remote Desktop from windows to Linux
- How to create a remote desktop user
- Remote Desktop from Windows to Linux
- Remote Desktop? HOW?
- How to speed up Remote Desktop Connection in Win7
- How to use sessions
- Connect to a Windows Desktop from Ubuntu via Remote Desktop Connection
- Connect to a Windows Desktop from Ubuntu via Remote Desktop Connection
- Ubuntu Tip:How to show desktop from command line
- How to call function from register view
- how to view bitmaps from memory dump
- Quartz.Net Client Connect/Disconnect from Remote server.
- How to lock computer in Remote Desktop Connection?(如何给远程桌面锁屏?)
- How to shutdown or reboot the machine on remote desktop connection?
- (OK) rdesktop - How to Use Remote Desktop (rdesktop) in Redhat/Fedora/CentOS
- Secure Remote Access from Your Desktop
- How to use adb to connect/disconnect device
- PHP获取随机数字和字母的方法大全
- 如何打patch
- HMAC_SHA1和SHA1的区别
- Iphone 之Timer
- Struts2的配置文件中配置result时传中文参数的问题
- How to View / Disconnect Remote Desktop Sessions from Commandline
- extgridpanel编辑保存数据
- MongoDB的使用技巧
- 快速排序算法-c#版
- 黑马程序员--Collection集合
- 怎样去除EXCEL中的重复行
- vim cscope
- ext gridpanel plugin rowediting编辑保存
- 介绍QSizePolicy::SizeType(zz)



