sha1withRSA md5withRSA分析
来源:互联网 发布:中级会计合并报表知乎 编辑:程序博客网 时间:2024/06/05 22:56
sha1withRSA哈希算法分析
参考资料
http://stackoverflow.com/questions/7646259/can-any-one-tell-what-i2d-x509-sig-function-do
http://www.cnblogs.com/adylee/archive/2009/08/03/1537813.html
提问帖子
can any one tell what i2d_X509_SIG() function do..?
i am using openssl 0.9.8g. inside RSA_verify() function decrypoted data is given to the d21_X509_SIG function. what does this function do and why we are doing this step while signing and verifying the signature
我正在使用openssl 0.98g.RSA_verify()函数解密数据调用了d2i_x509_sig函数,这个函数到底实现了什么,我们正在做签名和验签的项目。(译者:翻译不好见笑了)
opensslasked Oct 4 '11 at 10:08
1 Answer
The signature is actually not just for the hash (e.g. SHA-256), but for a data structure containing the hash plus some metadata (which hashing algorithm, some parameters and the hash length).That's why after decrypting, the data is decoded into a X509_SIG object and the actual comparison against the reference only performed on sig->digest->data.
这个签名事实上不仅是哈希(例如,SHA-256),而是一个哈希加上一些数据元素(哈希算法、一些参数和哈希长度)。这就是为什么解密到X509_SIG结构的和
sig->digest->data的数据不一致。
示例数据一
-------------------------------------------------------------------------------------------------------------------------------------------
哈希算法:sha1
签名
3eda2b913d484b2ec347fe68200f25aadc041e1d199e1f288178bcbd08ad8d7009c17ac44d4de88286b8430553ba61948d317d1c06bd9b3359a08a57e9ce22503e982840b8b6e392ba4d793c5a3012f42edc88daf92376c1efe099ba4f9a045b1fe26c80290bcafe93f438aa2854eb89398896686b6f08932c7c26e7463154920bfeb75726cae1fdba3d26f2a11313def6b4b2c4cf8716c50403c0c928affda0652671dcd5cc66c72fd89d635850179dafe0adfb211e470ac5c9ee39ff012b44d0a9b707f96356f6f1e0ecb85a8ed18951bec317d30af0fa7998dc946123b7e2900600f65e2d66d089602c7b2aae713b55f9575a69ac4011080c24b877ad60bb
公钥数据
3082010a0282010100a01ba9a2d772a1959533752c64f5cee4b5534e14c605b297bcbc23c6d4e9d083ffc3238c95a2c881f989106fec5dc4427ffb4b9358d6ded2ae7d87b8e447b597c921ae6054c77a2545283778d297ade3b15e77df0cd2eba51e8224ff0ca5c970a0e170134195e9c99ba4568f9c7295343c442447015e40d867f2db8a47ac56f7ec4e3596c3bc04e7c9e0a7a58f0ff3070b681017e45fea4f55a0e6e5ff28169f66b4b2da919229427be4be6c7ddb4c69270399bf0e3d990f67e116ddce96f7af323eb8373cf81d6c6118d2c32fffb16ff3d055e4cf1276a0a9e172fb6a17f016638ecf855c6e05b41253af84916c3da54de4a673d1ffe6c44b343fa367ba890f0203010001
解密结果
0001ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff003021300906052b0e03021a050004149bb631ae07153885e2d3ae693f0ff86ebf5d6f51
3021300906052b0e03021a050004149bb631ae07153885e2d3ae693f0ff86ebf5d6f51(35字节 ? + 哈希值20字节)
sha1哈希值应该是20字节
数据拆分(ASN.1 结构)
30(类型Sequence) 21(总长度) 30(类型Sequence) 09(长度) 06052b0e03021a 05(类型NULL)00(长度为0) 04(类型字符串) 14(长度) 9bb631ae07153885e2d3ae693f0ff86ebf5d6f51(20字节哈希值)
示例数据二
----------------------------------------------------------------------------------------
为了验证X509_sign调用PKCS#11接口的情况,自己实现了一个PKCS#11的包装壳(68个导出函数),实现时注意C_GetFunctionList应该指向本包装壳的函数,不然错误的使用实际的C_GetFunctionList作返回结构便也就失去意义了。X509_sign的调用方式还是不同的,java中如果使用SHA1WithRSA传入到PKCS#11接口的C_Sign或者C_SignUpdate的数据是完整的明文,但是X509_sign传入的是一个ASN.1 Sequence的一个结构,结构中包含待签名数据的摘要散列。
举例来说:
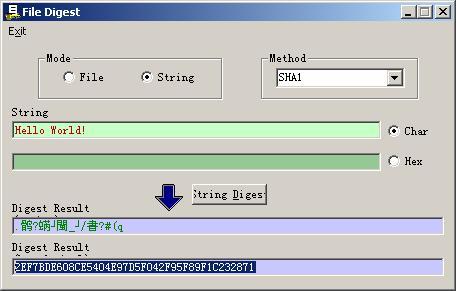
待加密的数据是Hello World! ,在C_Sign传入的数据中就可以发现Hello World!的SHA-1的摘要散列。
待加密:Hello World!
SHA-1: 2EF7BDE608CE5404E97D5F042F95F89F1C232871
C_Sign:
30 21 30 09 06 05 2b 0e 03 02 1a 05 00 04 14 2e f7 bd e6 08 ce 54 04 e9 7d 5f 04 2f 95 f8 9f 1c 23 28 71
使用ASN.1dump来观察就看的更加清楚了。
帖子截图:
- sha1withRSA md5withRSA分析
- DELPHI实现标准SHA1WithRSA、MD5WithRSA算法
- java中数字签名MD5withRSA和SHA1withRSA
- md5WithRSA
- C# MD5withRSA
- SHA1WithRSA 数字签名
- C#实现MD5WITHRSA签名
- 数字签名算法为:MD5withRSA
- 数字签名算法中MD5withRSA
- SHA1WithRSA 验证数字签名
- SHA1WithRSA算法-简介
- Sha1WithRSA签名的问题
- java SHA1WithRSA 算法
- MD5withRSA签名 DES加密解密
- php实现MD5withRSA签名算法
- golang 支付宝SHA1withRSA加密
- SHA1WithRSA签名使用openssl 实现
- C#实现标准JAVA的Md5withRsa算法
- 乱码 Remember
- 《编程人生》部分笔记摘要及我的体会—引领大师编程智慧
- win7下装ubuntu
- Python指南——类
- Android4.2多媒体media相关源码目录
- sha1withRSA md5withRSA分析
- 【数据结构&&算法】堆排序
- 关于内存泄漏
- iOS-网络流量统计
- 基础加强____【反射的作用__实现框架功能】
- poj 2965
- Hadoop WritableComparable接口收集的知识
- 说说android端实现Airplay多屏互动(二)
- JQuery实战总结









