The Open Source Interconnection (OSI) Model
来源:互联网 发布:vb源码下载 编辑:程序博客网 时间:2024/04/30 08:08
The OSI model is a layered model that describes how information moves from an application running on one networked computer to an application running on another networked computer. Think of it this way, the OSI model describes the steps to be used to transfer data from one networked device to another. Easy.
The model is divided into seven layers, as shown below. If you are serious about learning networking and information security, my advice is to memorize this image. I know it looks long and complicated at first, and trust me it is. But the more you use this (and you will) the faster it will come to you.
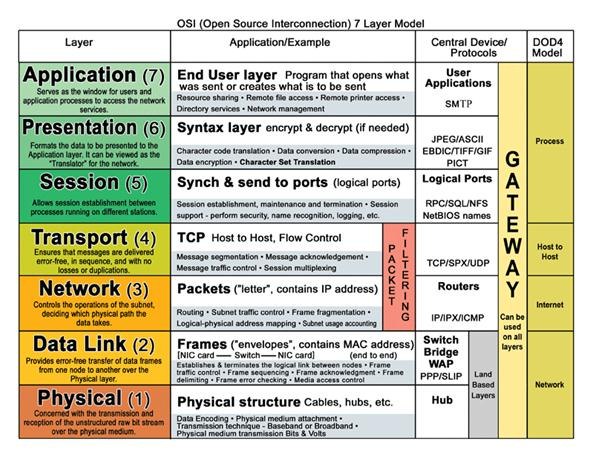
The reason for using a layered networking approach is that a layered model takes a task, such as data communications, and breaks it into a series of tasks, activities or components, each of which is defined and developed independently. OSI layers also allow extensibility. New protocols and other network services are generally easier to add to a layered architecture.
The basic idea behind the OSI reference model is this—Each layer is in charge of some kind of processing and each layer only talks to the layers immediately below and above it. For example, the sixth layer will only talk to the seventh and fifth layers, and never directly with the first layer. Remember this and it gets easy.
When your computer is transmitting data to the network, one given layer will receive data from the layer above, process what it received, add some control information to the data that this particular layer is in charge of, and send the new data with this new control information added to the layer below.
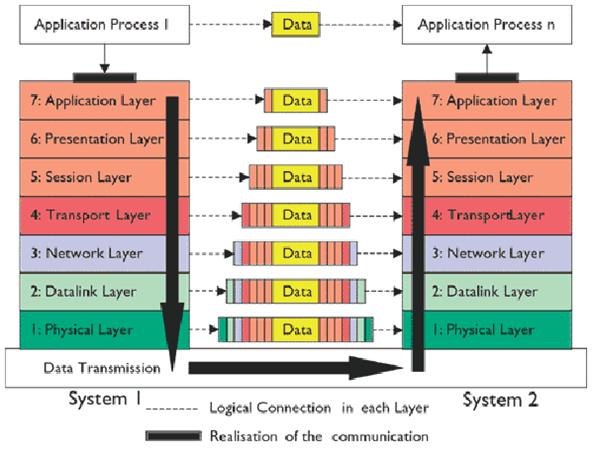
When your computer is receiving data, the contrary process will occur. One given layer will receive data from the layer below, process what it received, remove control information from the data that this particular layer is in charge of, and send the new data without the control information to the layer above.
What's important to keep in mind is that each layer will add or remove control information that it is in charge of. An acronym to help remember the model from bottom to top is “Please Do Not Throw Sausage Pizza Away.”
Layer 1: Physical
The physical layer describes the physical medium that data travels through. Think Ethernet cables, Network Interface Controllers, and things of the like. It also provides the interface between network and network communication devices.
Layer 2: Datalink
The datalink layer is where the network packets are translated into raw bits (00110101) to be transmitted on the physical layer. This is also a layer that uses the most basic addressing scheme, Media Access Control addresses. Think of a MAC address like a diver's license number—it's just a number that is unique from anyone else's.
Now, think of an IP address like a person's mailing address. The mailing address groups people into zones by using the zip code, city, state, and street identifiers.
Summary of Layer 1 and 2
When a network card receives a stream of bits over the network, it receives the data from the wires (the first layer), then the second layer is responsible for making sense of these 1s and 0s. The second layer first checks the destination MAC address in the frame to make sure the data was intended for that computer. If the destination MAC address matches the MAC address of the network card, it carries on.
Layer 3: Network
The network layer determines how data transmits between network devices. It also translates the logical address into the physical address (computer name into MAC address). It's also responsible for defining the route, managing network problems, and addressing. Routers also work on the network layer.
The most important part of understanding this third layer is knowing that routers make decisions based on layer three's information. Routers are machines that decide how to send information from one logical network to another. Routers understand the Internet Protocol (IP) and base routing decisions on that information.
Layer 4: Transport
The transport layer accepts data from the session layer and breaks it into packets and delivers these packets to the network layer. It's the responsibility of the transport layer to guarantee successful arrival of data at the destination device. Transport Layer Security also runs on this layer.
Layer 5: Session
The session layer manages the setting up and taking down of the association between two communicating end points, called a connection. A connection is maintained while the two end points are communicating back and forth.
Another way to look at it—picture your computer. You're browsing the web, downloading from an FTP server, streaming some music, and who knows what else, all at the same time. All that data is coming into your computer, but it would make little sense if the FTP data was being sent to your Pandoratab, wouldn't it? It's in this layer that ports are used and that data is properly directed.
Layer 6: Presentation
The presentation layer resolves differences in data representation by translating from application to network format, and vice versa. It works to transform data into the form that the application layer can accept. Remember, each layer can only 'talk' to the layer above and below it.
This layer is mainly concerned with the syntax and semantics of the information transmitted. For outgoing messages, it converts data into a generic format for the transmission. For the incoming messages, it converts the data to a format understandable to the receiving application. This layer also formats and encrypts data to be sent across a network, providing freedom from compatibility problems and issues.
Layer 7: Application
The application layer is the top layer of the model. It provides a set of interfaces for applications to obtain access to networked services. This layer also provides application access security checking and information validation.

Common services that will seem familiar include streaming music, email, and online games. When you think of the application layer, think of just that—applications.
From: http://null-byte.wonderhowto.com/how-to/spy-your-buddys-network-traffic-intro-wireshark-and-osi-model-0133807/
- The Open Source Interconnection (OSI) Model
- OSI(Open Systems Interconnection)
- 1.OSI(开放系统互连(Open System Interconnection))模型
- The seven layer of the osi model
- the Open Source Community
- The Open Source Definition
- Open at the source.
- The Cisco Three Layer Hierarchical Model vs the OSI Model
- Introduction to the OSI Reference Model
- The history of open source
- Open Source: Voices from the Open Source Revolution
- Code reading: the open source perspective
- The Open Source Definition 开源定义
- The Open Source Development Environment for .NET
- Code Quality: The Open Source Perspective
- Understanding the PureMVC Open Source Framework1
- Understanding the PureMVC Open Source Framework2
- The open source project in China
- TCP/IP 详解卷一 - 第2章 链路层
- 雷军不是个好程序员
- 【Unity】NGUI实现技能冷却脚本
- LeetCode125——Valid Palindrome
- Hadoop报错信息:Job not successful. Error: # of failed Map Tasks exceeded allowed limit. FailedCount: 4.
- The Open Source Interconnection (OSI) Model
- ios去掉字符串中的html标签的方法
- 【设计模式】-模板方法模式(Template)
- Unity 通过脚本修改源资源
- postgres函数
- winows运行时应用生命周期
- c++_primer_exercise_1435_1436
- nodejs使用express,express版本3.5.3使用中间件app.user(express.multipart())异常问题
- myeclipse8.5发布maven web项目


