ESAPI = Enterprise Security API
来源:互联网 发布:信赖域反射算法 编辑:程序博客网 时间:2024/05/22 11:31
ESAPI简介
url:http://blog.sina.com.cn/s/blog_435ae8c80100jom4.html
ESAPI是一个免费、开源的Web应用程序安全控制组件,可以帮助编程人员开发低风险应用程序。
ESAPI是OWASP组织的一个开源项目,网址是:http://www.owasp.org/index.php/ESAPI
ESAPI很适合一个新的开发项目的安全组件,各版本的ESAPI包含如下基本设计:
1.具有一个安全接口集;2.对每一种安全控制有一种参考实现;3.对每一种安全控制可以有你自己的实现方法。很多著名的大公司开始将ESAPI作为自己保障Web应用程序安全的手段,包括美国运通公司,Apache基金会,世界银行等。
ESAPI对常见安全漏洞都提供对应的安全控制实现方法:
ESAPI使用示例:
使用ESAPI防止XSS的做法: String safe = ESAPI.encoder().encodeForHTML( request.getParameter("input") ); 对用户输入“input”进行HTML编码,防止XSS。
System.out.println(ESAPI.encoder().encodeForHTML("<a href='sdfs'></a> < script > alert(); </ script >"));输出的结果
<a href='sdfs'></a> < script > alert(); </ script >使用ESAPI防止ORACLE数据库SQL注入的做法:
String sqlStr=“select name from tableA where id=”+ ESAPI.encoder().encodeForSQL(ORACLE_CODEC,validatedUserId) +“and date_created”='“ + ESAPI.encoder()。encodeForSQL(ORACLE_CODEC,validatedStartDate)+"'"; myStmt = conn.createStatement(sqlStr);补充: XSS又叫CSS (Cross Site Script) ,跨站脚本攻击。它指的是恶意攻击者往Web页面里插入恶意html代码,当用户浏览该页之时,嵌入其中Web里面的html代码会被执行,从而达到恶意攻击用户的特殊目的。
ESAPI = Enterprise Security API
posted @ 2009-01-16 16:10 CoderZh
url: http://www.cnblogs.com/coderzh/archive/2009/01/16/1377140.html
下面是OWASP里的说明,其实简单一点来说,ESAPI就是为编写出更加安全的代码设计出来的一些API,方便使用者调用,从而方便的编写安全的代码。它本身是开源的,同时提供JAVA版本和.NET版本。
代码下载地址:http://code.google.com/p/owasp-esapi-java/
ESAPI介绍的PPT:http://owasp-esapi-java.googlecode.com/files/OWASP%20ESAPI.ppt
下图显示了提供的API与OWASP列出的10个安全问题的涵盖关系:
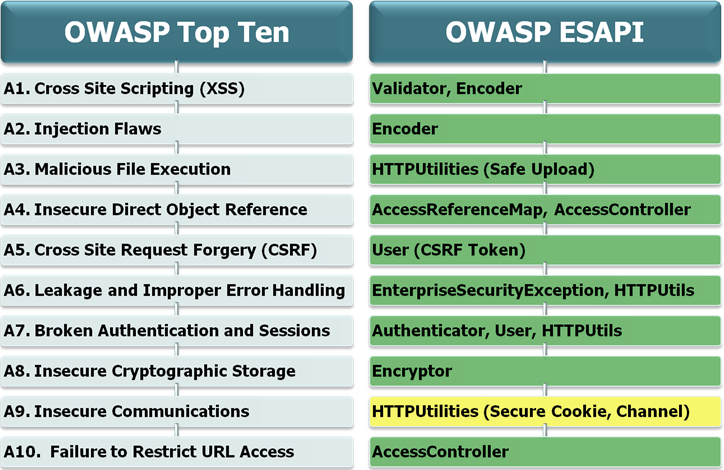
--------------------------------------------------------- 来自 owasp --------------------------------------------------------------------------
Watch the Video

What is ESAPI?
The ESAPI is a free and open collection of all the security methods that a developer needs to build a secure web application. You can just use the interfaces and build your own implementation using your company's infrastructure. Or, you can use the reference implementation as a starting point. In concept, the API is language independent. However, the first deliverables from the project are a Java API and a Java reference implementation. Efforts to build ESAPI in .NET and PHP are already underway.

Why ESAPI?
Unfortunately, the available platforms, frameworks, and toolkits (Java EE, Struts, Spring, etc...) simply do not provide enough protection. This leaves developers with responsibility for designing and building security mechanisms. This reinventing the wheel for every application leads to wasted time and massive security holes.
The cost savings through reduced development time, and the increased security due to using heavily analyzed and carefully designed security methods provide developers with a massive advantage over organizations that are trying to deal with security using existing ad hoc secure coding techniques. This API is designed to automatically take care of many aspects of application security, making these issues invisible to the developers.

Where did ESAPI come from?
The OWASP ESAPI project is led by Jeff Williams, who serves as the volunteer chair of OWASP and is the CEO of Aspect Security. Jeff is a software developer who has specialized in application security since 1995. The ESAPI is the result of over a decade of code review and penetration testing of critical enterprise applications. If you'd like to volunteer to help on the project, you can contact him at jeff.williams@owasp.org.
More information about the ESAPI can be found in the ESAPI PowerPoint presentation
- ESAPI = Enterprise Security API
- esapi api
- Enterprise Library Security Application Block
- Best Practices for Enterprise Security
- Enterprise Library 2.0 -- Security Application Block
- Enterprise Library 2.0 -- Security Application Block
- Enterprise Library 2.0 -- Security Application Block
- Advances in Enterprise Information Technology Security
- Enterprise Security: The Manager's Defense Guide
- Advances in Enterprise Information Technology Security
- ESAPI WAF
- ESAPI简介
- ESAPI使用方法
- ESAPI简介
- spring-security api
- Oracle Security API - FND_FUCTION.TEST
- Spring Security 4 Rest API
- Openstack api security testing tools
- Error: INVALID_STATE_ERR解决方案
- 摄像机返回值data为空可用Uri获取图片
- Mongoose的用法笔记
- Mongodb
- LintCode-删除排序链表中的重复元素
- ESAPI = Enterprise Security API
- javascript
- Android自定义进度条
- 3wetfqwerqwer
- 2015-10-23
- 关于导入APACHE POI包之后的错误
- Move Zeroes
- sqlplus 上下左右及回退乱码
- LuaJava:一点一点写Example 1


