nmap中的Idle scan
来源:互联网 发布:百度网盘显示网络异常1 编辑:程序博客网 时间:2024/05/17 22:25
最近用到nmap,感觉功能很强大,并开始深入学习,现将其中端口探测部分的一种Idel scan技术的理解记录如下(需要一些TCP/IP方面的知识):
1.理论基础
a. 每个IP包都有帧ID,记作IP ID
b. TCP正常建立链接的时候,第一步是主机A从端口X发给主机B端口Y一个 SYN,第二步是B回应A一个SYN/ACK,第三步是A回B一个ACK,连接建立了。如果A没有发给B一个SYN,而B发给A了一个SYN/ACK,那么A就会发给B一个RST
c. 大部分主机的TCP/IP协议实现中,RST中的IP ID是递增的,增加的单位是1,即incremental
2。TCP Idle scan原理和步骤
a. 这里需要三台主机,一台攻击者,一台没有什么网络流量的空闲主机,还有就是我们的目标主机
b. 目标的某个端口的状态可能是打开、关闭或则被过滤,在遇到我们的Idle scan的时候,不同状态的端口的scan的结果是不一样,由此来判断端口是否是打开的
c. 具体步骤为:
(1)找到一台空闲主机,并从攻击主机发给空闲主机一个SYN/ACK,获得并记录空闲主机的RST的IP ID
(2)在攻击者的主机上虚构一个从空闲主机到目标主机的一个SYN,于是根据目标主机的目标端口状态,如果目标主机的目标端口打开,将会发给空闲主机的一个SYN/ACK,所以空闲主机将会发给目标主机一个RST,否则不会发送RST
(3)再次从攻击主机发给空闲主机SYN/ACK,检查RST的IP ID,如果IP ID比第一步记录下的增加了二,则说明第二步中空闲主机给目标主机发送了一个RST,目标主机的目标端口处于打开状态,否则为没打开
根据目标主机的目标端口的不同状态,可得一下三附图:
 the attacker,
the attacker,  the zombie, and
the zombie, and  the target.
the target.
Figure 2.1. Idle scan of an open port
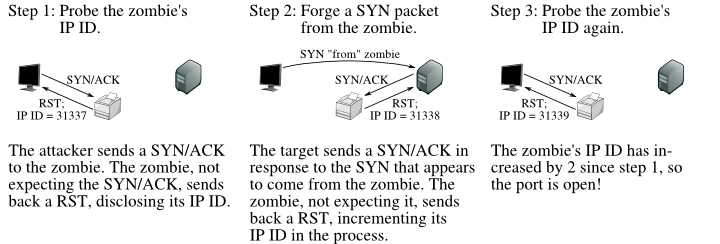
Figure 2.2. Idle scan of a closed port
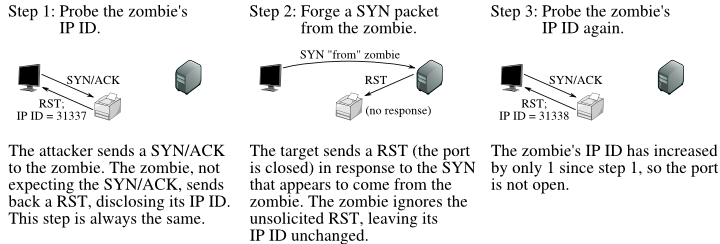
Figure 2.3. Idle scan of a filtered port

3. nmap中的实现
a. 选择空闲主机时,尽量选择离攻击主机和目标主机比较近的,这样可以增加nmap的性能和可靠性,nmap的-iR选项可以用来随机选择寻找的主机,-O和-v可以查看主机的IP ID增长的方式是否为incremental;在一种方法就是使用nmap的--script选项,指定脚本:ipidseq,如:nmap --script ipidseq -iR 5 -O -v
b. 一个实例:
nmap -sI Zombie -Pn -p20-25,110 -r --packet-trace -v Target未完待续!
详细请参考:http://nmap.org/book/idlescan.html
- nmap中的Idle scan
- TCP Idle Scan
- idle scan相关阅读
- Nmap - scan host with VPN
- Nmap Full Web Vulnerable Scan
- 渗透测试之Nmap命令(三) idle 扫描
- 渗透测试之Nmap命令(三) idle 扫描
- kernel中的idle分析
- Netty中的Idle事件
- lk中的idle thread
- HBase中的Scan操作
- Nmap
- nmap
- nmap
- NMap
- nmap
- Nmap
- nmap
- JAVA基础之理解JNI原理
- Android学习札记28:深入理解Android中的消息处理机制——Thread、Looper、MessageQueue和Handler(2)
- 关于 法向量 的世界空间变换矩阵
- 因为启用了google的安全搜索功能 **已被google过滤掉 的解决办法
- 比较有用的linux博客
- nmap中的Idle scan
- 对几个问题的思考
- T-SQL 计算固定资产折旧(双倍余额法)
- mongodb集群搭建
- eclipse3.7安装maven插件失败问题解决
- postfix sasl身份验证
- Cyrus-SASL 安装
- hdu 4308 Saving Princess claire_ 广搜 多校联合赛第七题
- linux中如何重新获取丢失的密码


