双SVTI高可用性 VPN的最佳解决方案
来源:互联网 发布:linux sh文件怎么运行 编辑:程序博客网 时间:2024/04/27 05:09
高可用性VPN的最佳解决方案
1、方案介绍
本章主要介绍在纯cisco设备的情况下,一种简单而又实用的高可用性的ipsec最佳解决方案。
2、拓扑图
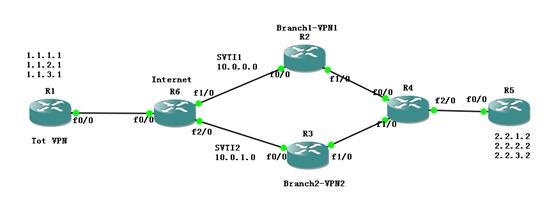
方案拓扑图解析
上图为高可用性站点到站点ipsec vpn的最佳解决方案接线图,从左到右依次是总部公司的路由器,internet路由器,分部master路由,分部slave路由器,公司网络环境,从R4以后就模拟整个公司的核心网络。
该拓扑最核心的地方在于在总部和分部之间建立两条SVTI通道,然后全网运行EIGRP,选择EIGRP是因为收敛速度较快,隧道接口10.0.0.0/24和10.0.1.0/24分别都运行EIGRP,并实现负载均衡。这里有一个非常大的特点,就是我们用EIGRP动态路由技术替代了所谓的DPD和RRI技术,如果动态路由出现了问题,那么邻居关系就会消失,自然中心站点的路由也会消失,因此自然就不会将加密的数据包送到这个网关。
3、configure
R1#show run
Building configuration...
Current configuration : 1779 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
!
!
ip cef
no ip domain lookup
ip tcp synwait-time 5
!
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 26.26.26.2
crypto isakmp key cisco address 36.36.36.3
!
!
crypto ipsec transform-set mytrans esp-3desesp-md5-hmac
!
crypto ipsec profile ipsecprof
settransform-set mytrans
!
!
!
!
!
interface Loopback1
ipaddress 1.1.1.1 255.255.255.255
!
interface Loopback2
ipaddress 1.1.2.1 255.255.255.255
!
interface Loopback3
ipaddress 1.1.3.1 255.255.255.255
!
interface Tunnel0
ipaddress 10.0.0.1 255.255.255.0
tunnel source 16.16.16.1
tunneldestination 26.26.26.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsecprof
!
interface Tunnel1
ipaddress 10.0.1.1 255.255.255.0
tunnel source 16.16.16.1
tunnel destination 36.36.36.3
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsecprof
!
interface FastEthernet0/0
ipaddress 16.16.16.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
noip address
shutdown
duplex auto
speed auto
!
router eigrp 100
network 1.1.1.0 0.0.0.255
network 1.1.2.0 0.0.0.255
network 1.1.3.0 0.0.0.255
network 10.0.0.0 0.0.0.255
network 10.0.1.0 0.0.0.255
noauto-summary
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 16.16.16.6
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
End
R6#show run
Building configuration...
Current configuration : 877 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R6
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
!
!
ip cef
no ip domain lookup
!
!
!
!
!
ip tcp synwait-time 5
!
!
!
!
!
interface FastEthernet0/0
ipaddress 16.16.16.6 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ipaddress 26.26.26.6 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet2/0
ipaddress 36.36.36.6 255.255.255.0
duplex auto
speed auto
!
no ip http server
no ip http secure-server
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
R2#show run
Building configuration...
Current configuration : 1316 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
!
!
ip cef
no ip domain lookup
!
!
ip tcp synwait-time 5
!
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 16.16.16.1
!
!
crypto ipsec transform-set mytrans esp-3desesp-md5-hmac
!
crypto ipsec profile ipsecprof
settransform-set mytrans
!
!
!
!
!
interface Tunnel0
ipaddress 10.0.0.2 255.255.255.0
tunnel source 26.26.26.2
tunnel destination 16.16.16.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsecprof
!
interface FastEthernet0/0
ipaddress 26.26.26.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ipaddress 24.24.24.2 255.255.255.0
duplex auto
speed auto
!
router eigrp 100
network 10.0.0.0 0.0.0.255
network 24.24.24.0 0.0.0.255
noauto-summary
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 26.26.26.6
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
End
R3#show run
Building configuration...
*Mar 1 01:43:25.395: %SYS-5-CONFIG_I: Configured from console by console
Current configuration : 1316 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
!
!
ip cef
no ip domain lookup
ip tcp synwait-time 5
!
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 16.16.16.1
!
!
crypto ipsec transform-set mytrans esp-3desesp-md5-hmac
!
crypto ipsec profile ipsecprof
settransform-set mytrans
!
!
!
!
!
interface Tunnel1
ipaddress 10.0.1.2 255.255.255.0
tunnel source 36.36.36.3
tunnel destination 16.16.16.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsecprof
!
interface FastEthernet0/0
ipaddress 36.36.36.3 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ipaddress 34.34.34.3 255.255.255.0
duplex auto
speed auto
!
router eigrp 100
network 10.0.1.0 0.0.0.255
network 34.34.34.0 0.0.0.255
noauto-summary
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 36.36.36.6
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
R3#
R4#show run
Building configuration...
Current configuration : 1003 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R4
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
!
!
ip cef
no ip domain lookup
!
!
--More--
*Mar 1 01:43:55.363: %SYS-5-CONFIG_I: Configured from console ! e
!
ip tcp synwait-time 5
!
!
!
!
!
interface FastEthernet0/0
ipaddress 24.24.24.4 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ipaddress 34.34.34.4 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet2/0
ipaddress 45.45.45.4 255.255.255.0
duplex auto
speed auto
!
router eigrp 100
network 24.24.24.0 0.0.0.255
network 34.34.34.0 0.0.0.255
network 45.45.45.0 0.0.0.255
noauto-summary
!
no ip http server
no ip http secure-server
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
End
R5#show run
Building configuration...
Current configuration : 1018 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R5
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
!
!
ip cef
no ip domain lookup
!
!
--More--
*Mar 1 01:44:28.823: %SYS-5-CONFIG_I: Configured from console ! e
!
ip tcp synwait-time 5
!
interface Loopback1
ipaddress 2.2.1.2 255.255.255.255
!
interface Loopback2
ipaddress 2.2.2.2 255.255.255.255
!
interface Loopback3
ipaddress 2.2.3.2 255.255.255.255
!
interface FastEthernet0/0
ipaddress 45.45.45.5 255.255.255.0
duplex auto
speed auto
!
router eigrp 100
network 2.2.1.0 0.0.0.255
network 2.2.2.0 0.0.0.255
network 2.2.3.0 0.0.0.255
network 45.45.45.0 0.0.0.255
noauto-summary
!
no ip http server
no ip http secure-server
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
R5#
4、测试
我们会在R1上看到有两条通往目的网络的路由,且能实现负载均衡
R1#show ip route
Codes: C - connected, S - static, R - RIP,M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 16.16.16.6 tonetwork 0.0.0.0
34.0.0.0/24 is subnetted, 1 subnets
D 34.34.34.0 [90/297246976] via 10.0.1.2, 00:33:52, Tunnel1
16.0.0.0/24 is subnetted, 1 subnets
C 16.16.16.0 is directly connected, FastEthernet0/0
1.0.0.0/32 is subnetted, 3 subnets
C 1.1.1.1 is directly connected, Loopback1
C 1.1.3.1 is directly connected, Loopback3
C 1.1.2.1 is directly connected, Loopback2
2.0.0.0/32 is subnetted, 3 subnets
D 2.2.2.2 [90/297377536] via 10.0.1.2, 00:33:53, Tunnel1
[90/297377536] via 10.0.0.2,00:33:53, Tunnel0
D 2.2.3.2 [90/297377536] via 10.0.1.2, 00:33:53, Tunnel1
[90/297377536] via 10.0.0.2,00:33:53, Tunnel0
D 2.2.1.2 [90/297377536] via 10.0.1.2, 00:33:54, Tunnel1
[90/297377536] via 10.0.0.2,00:33:54, Tunnel0
24.0.0.0/24 is subnetted, 1 subnets
D 24.24.24.0 [90/297246976] via 10.0.0.2, 00:33:54, Tunnel0
10.0.0.0/24 is subnetted, 2 subnets
C 10.0.0.0 is directly connected, Tunnel0
C 10.0.1.0 is directly connected, Tunnel1
45.0.0.0/24 is subnetted, 1 subnets
D 45.45.45.0 [90/297249536] via 10.0.1.2, 00:33:54, Tunnel1
[90/297249536] via 10.0.0.2,00:33:54, Tunnel0
S* 0.0.0.0/0 [1/0] via 16.16.16.6
R1#
R1#traceroute 2.2.2.2 source loopback 1
Type escape sequence to abort.
Tracing the route to 2.2.2.2
110.0.0.2 44 msec
10.0.1.2 44 msec
10.0.0.2 36 msec
234.34.34.4 40 msec
24.24.24.4 60 msec
34.34.34.4 36 msec
345.45.45.5 76 msec 68 msec 60 msec
切换down掉R2的f0/0口,观察现象
R1#traceroute 2.2.2.2 source loopback 1
Type escape sequence to abort.
Tracing the route to 2.2.2.2
110.0.1.2 52 msec 40 msec 20 msec
234.34.34.4 44 msec 68 msec 32 msec
345.45.45.5 96 msec 88 msec 60 msec
R1#
能直接切换到34.34.34.4的备用链路上
Mar 1 01:57:06.051: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 100: Neighbor 10.0.0.2(Tunnel0) is up: new adjacency
当R2恢复正常后,新邻居再次建立,我们再看
R1#traceroute 2.2.2.2 source loopback 1
Type escape sequence to abort.
Tracing the route to 2.2.2.2
110.0.1.2 44 msec
10.0.0.2 60 msec
10.0.1.2 40 msec
224.24.24.4 60 msec
34.34.34.4 56 msec
24.24.24.4 40 msec
345.45.45.5 44 msec 88 msec 60 msec
R1#
链路又重新回到负载均衡状态。。。
==============================================================================================================
5、加解密流量
R1#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 16.16.16.1
protected vrf: (none)
local ident (addr/mask/prot/port):(0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 26.26.26.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 892, #pkts encrypt: 892, #pkts digest: 892
#pkts decaps: 770, #pkts decrypt: 770, #pkts verify: 770
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 16.16.16.1, remote crypto endpt.: 26.26.26.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xCF74CA99(3480537753)
inbound esp sas:
spi: 0x42A925C7(1118381511)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4553001/279)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xCF74CA99(3480537753)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: SW:3, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4552992/265)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 16.16.16.1
protected vrf: (none)
local ident(addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 36.36.36.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 1188, #pkts encrypt: 1188, #pkts digest: 1188
#pkts decaps: 1317, #pkts decrypt: 1317, #pkts verify: 1317
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 16.16.16.1, remote crypto endpt.: 36.36.36.3
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x7C3B9CEE(2084281582)
inbound esp sas:
spi: 0x2F87FB44(797440836)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: SW:4, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4482892/1480)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x7C3B9CEE(2084281582)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4482892/1478)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
- 双SVTI高可用性 VPN的最佳解决方案
- HA高可用性的IPSec VPN配置实例
- 集成ISA Server和RRAS实现具有高可用性和高安全性的站点间VPN
- 高可用性、负载均衡的mysql集群解决方案
- 高可用性、负载均衡的mysql集群解决方案 -- 2
- Linux高可用性解决方案Heartbeat的安装与配置
- 高可用性、负载均衡的mysql集群解决方案
- 高可用性、负载均衡的mysql集群解决方案
- 高可用性、负载均衡的mysql集群解决方案
- 高可用性、负载均衡的mysql集群解决方案介绍
- 高可用性、负载均衡的mysql集群解决方案
- 高可用性、负载均衡的mysql集群解决方案
- 高可用性、负载均衡的mysql集群解决方案
- 路由器SVTI 站点到站点VPN
- EF的高可用性
- ActiveMQ的高可用性
- 数据库高可用性解决方案优劣分析(转)
- Sql Server 2008 高可用性解决方案概述
- 基础的check
- 从键盘输入文件的结束符
- mysql命令行下处理存储过程
- Redis数据类型
- iOS7中容易被忽视的新特性
- 双SVTI高可用性 VPN的最佳解决方案
- Pascal's Triangle系列
- Uva10723 - Cyborg Genes
- 修改右下角"自豪地采用Wordpress bitnamiW"正确方法
- iOS抓包
- nginx常见的启动错误
- 无 99 美金证书联机开发
- VPN简单汇总总结
- ocr文字识别软件ABBYY FineReader介绍


