160个CrackMe 027 Cosh.1
来源:互联网 发布:淘宝一件代发供货平台 编辑:程序博客网 时间:2024/06/05 14:54
首先打开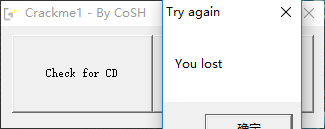
发现这是一个CD-check的题目
这里推荐一下《加密与解密 第三版》的5.7节CD-Check还有一个博客
CD-check
大家可以参考
之后PEID查,没有壳,C++程序,CD-Check我们只能够通过爆破:
OD运行:
接下来大致分成三种找到关键位置的方式:
1.正常运行:F9之后弹出对话框,我们点击Check for CD之后,弹出错误对话框,不点击确定,直接F12暂停程序之Alt+K找对话框的函数调用(这是弹出错误对话框类型的处理方式)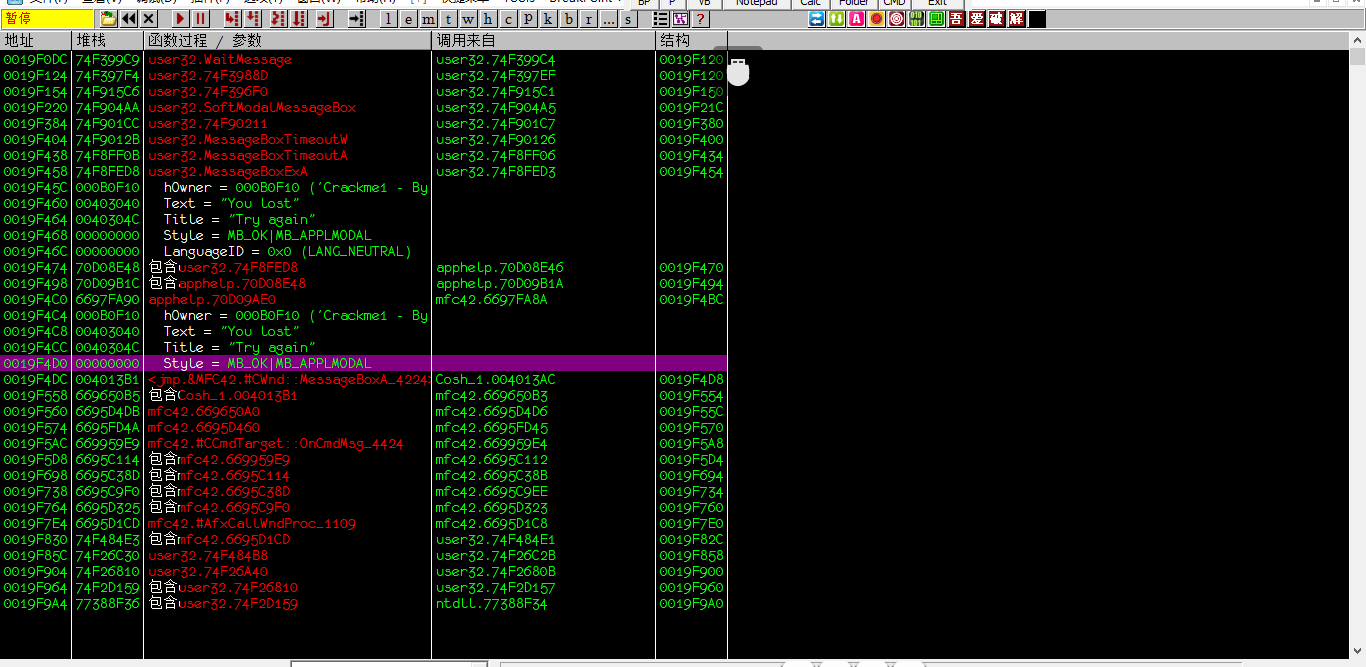
找到函数调用的部分,show call过去
2.既然是一个CD-Check那么我们就去找关键函数呗,GetDirvertypeA是获取磁盘驱动器类型的关键函数
OD之后,Crtl+N 查找所有调用函数模块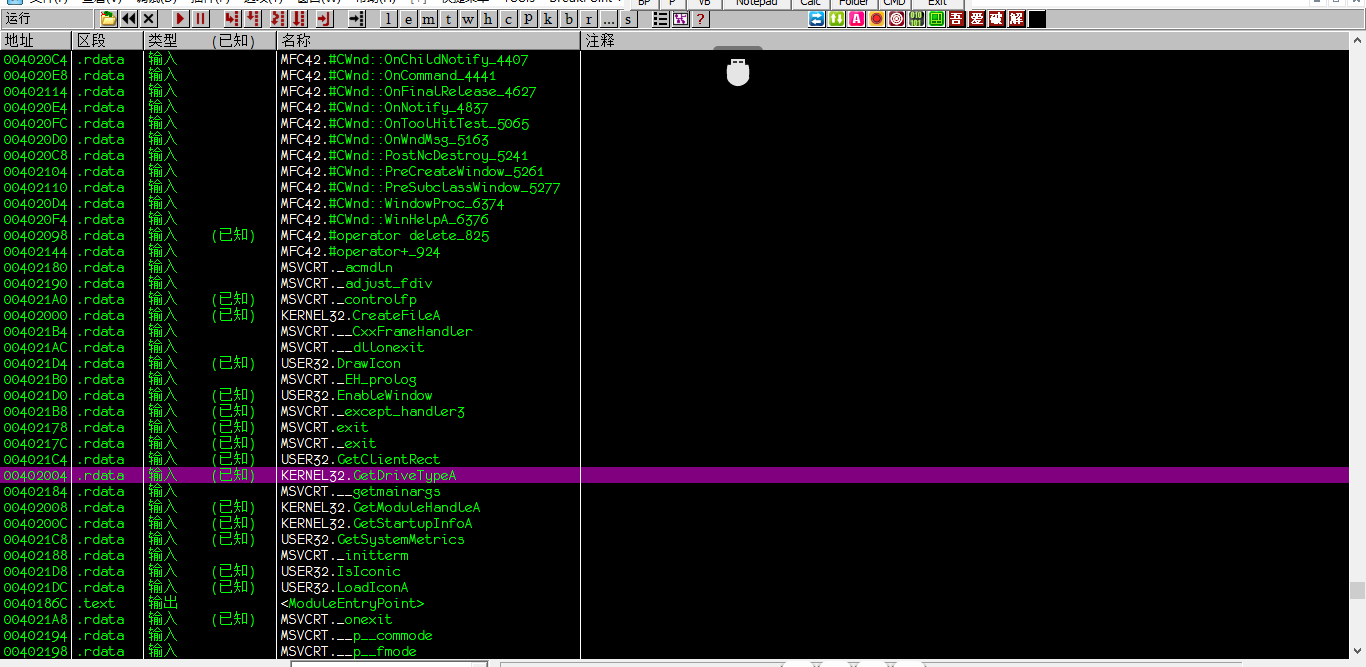
查看调用树,找到调用位置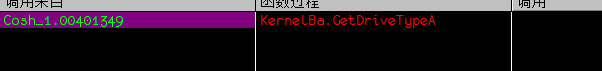
反汇编窗口跟随过去即可
3.最简单使用的,直接找参考文本字符串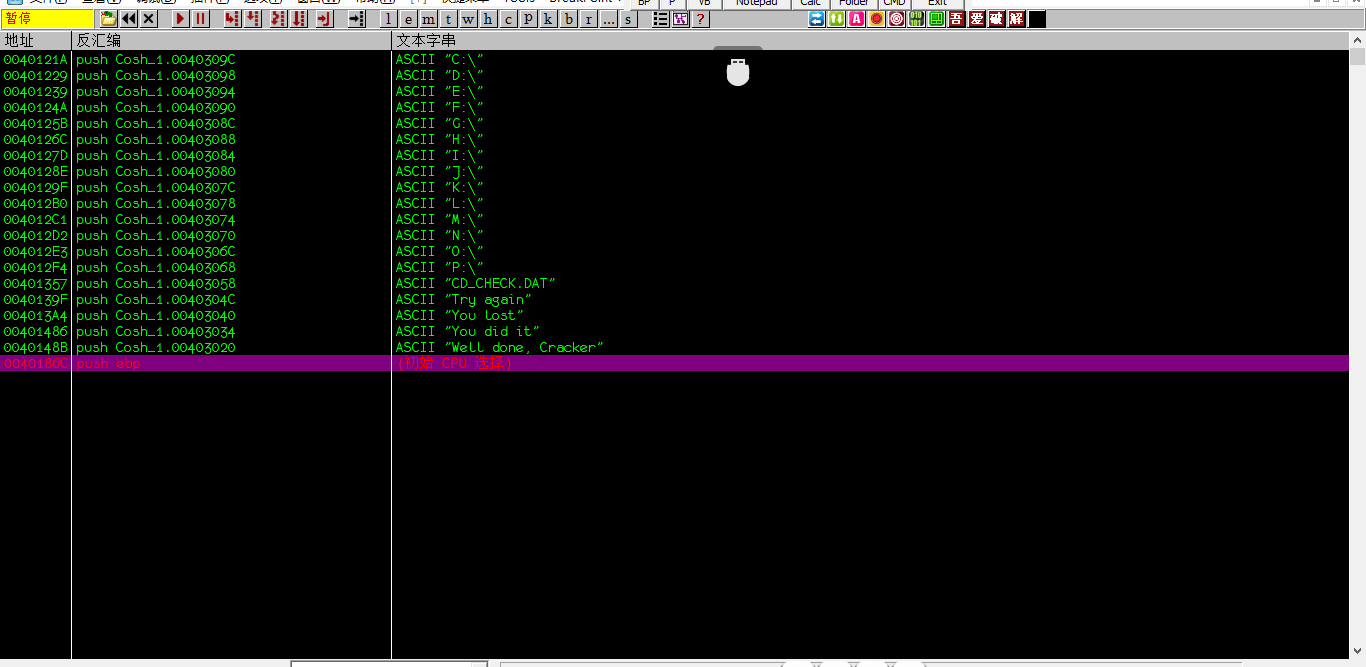
失败的成功一起找到,很简单
之后找到关键位置,找跳转语句就很轻松了
0040138C /0F84 F3000000 je Cosh_1.00401485 ; 跳转语句00401392 > |FF45 EC inc dword ptr ss:[ebp-0x14]00401395 . |83C7 04 add edi,0x400401398 . |837D EC 07 cmp dword ptr ss:[ebp-0x14],0x70040139C .^|75 9F jnz short Cosh_1.0040133D0040139E . |53 push ebx0040139F . |68 4C304000 push Cosh_1.0040304C ; ASCII "Try again"004013A4 . |68 40304000 push Cosh_1.00403040 ; ASCII "You lost"004013A9 > |8B4D E4 mov ecx,dword ptr ss:[ebp-0x1C]004013AC . |E8 D1020000 call <jmp.&MFC42.#CWnd::MessageBoxA_4224>004013B1 . |8D4D E8 lea ecx,dword ptr ss:[ebp-0x18]004013B4 . |C645 FC 0E mov byte ptr ss:[ebp-0x4],0xE004013B8 . |E8 DD020000 call <jmp.&MFC42.#CString::~CString_800>004013BD . |56 push esi ; Cosh_1.<ModuleEntryPoint>004013BE . |6A 01 push 0x1004013C0 . |8D45 DC lea eax,dword ptr ss:[ebp-0x24]004013C3 . |6A 04 push 0x4004013C5 . |50 push eax004013C6 . |C645 FC 0D mov byte ptr ss:[ebp-0x4],0xD004013CA . |E8 27030000 call Cosh_1.004016F6004013CF . |8D4D D8 lea ecx,dword ptr ss:[ebp-0x28]004013D2 . |C645 FC 0C mov byte ptr ss:[ebp-0x4],0xC004013D6 . |E8 BF020000 call <jmp.&MFC42.#CString::~CString_800>004013DB . |8D4D D4 lea ecx,dword ptr ss:[ebp-0x2C]004013DE . |C645 FC 0B mov byte ptr ss:[ebp-0x4],0xB004013E2 . |E8 B3020000 call <jmp.&MFC42.#CString::~CString_800>004013E7 . |8D4D D0 lea ecx,dword ptr ss:[ebp-0x30]004013EA . |C645 FC 0A mov byte ptr ss:[ebp-0x4],0xA004013EE . |E8 A7020000 call <jmp.&MFC42.#CString::~CString_800>004013F3 . |8D4D CC lea ecx,dword ptr ss:[ebp-0x34]004013F6 . |C645 FC 09 mov byte ptr ss:[ebp-0x4],0x9004013FA . |E8 9B020000 call <jmp.&MFC42.#CString::~CString_800>004013FF . |8D4D C8 lea ecx,dword ptr ss:[ebp-0x38]00401402 . |C645 FC 08 mov byte ptr ss:[ebp-0x4],0x800401406 . |E8 8F020000 call <jmp.&MFC42.#CString::~CString_800>0040140B . |8D4D C4 lea ecx,dword ptr ss:[ebp-0x3C]0040140E . |C645 FC 07 mov byte ptr ss:[ebp-0x4],0x700401412 . |E8 83020000 call <jmp.&MFC42.#CString::~CString_800>00401417 . |8D4D C0 lea ecx,dword ptr ss:[ebp-0x40]0040141A . |C645 FC 06 mov byte ptr ss:[ebp-0x4],0x60040141E . |E8 77020000 call <jmp.&MFC42.#CString::~CString_800>00401423 . |8D4D BC lea ecx,dword ptr ss:[ebp-0x44]00401426 . |C645 FC 05 mov byte ptr ss:[ebp-0x4],0x50040142A . |E8 6B020000 call <jmp.&MFC42.#CString::~CString_800>0040142F . |8D4D B8 lea ecx,dword ptr ss:[ebp-0x48]00401432 . |C645 FC 04 mov byte ptr ss:[ebp-0x4],0x400401436 . |E8 5F020000 call <jmp.&MFC42.#CString::~CString_800>0040143B . |8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C]0040143E . |C645 FC 03 mov byte ptr ss:[ebp-0x4],0x300401442 . |E8 53020000 call <jmp.&MFC42.#CString::~CString_800>00401447 . |8D4D B0 lea ecx,dword ptr ss:[ebp-0x50]0040144A . |C645 FC 02 mov byte ptr ss:[ebp-0x4],0x20040144E . |E8 47020000 call <jmp.&MFC42.#CString::~CString_800>00401453 . |8D4D AC lea ecx,dword ptr ss:[ebp-0x54]00401456 . |C645 FC 01 mov byte ptr ss:[ebp-0x4],0x10040145A . |E8 3B020000 call <jmp.&MFC42.#CString::~CString_800>0040145F . |8D4D A8 lea ecx,dword ptr ss:[ebp-0x58]00401462 . |885D FC mov byte ptr ss:[ebp-0x4],bl00401465 . |E8 30020000 call <jmp.&MFC42.#CString::~CString_800>0040146A . |834D FC FF or dword ptr ss:[ebp-0x4],-0x10040146E . |8D4D A4 lea ecx,dword ptr ss:[ebp-0x5C]00401471 . |E8 24020000 call <jmp.&MFC42.#CString::~CString_800>00401476 . |8B4D F4 mov ecx,dword ptr ss:[ebp-0xC]00401479 . |5F pop edi ; kernel32.740738F40040147A . |5E pop esi ; kernel32.740738F40040147B . |5B pop ebx ; kernel32.740738F40040147C . |64:890D 00000>mov dword ptr fs:[0],ecx ; Cosh_1.<ModuleEntryPoint>00401483 . |C9 leave00401484 . |C3 retn00401485 > \53 push ebx00401486 . 68 34304000 push Cosh_1.00403034 ; ASCII "You did it"0040148B . 68 20304000 push Cosh_1.00403020 ; ASCII "Well done, Cracker"00401490 .^ E9 14FFFFFF jmp Cosh_1.004013A9爆破,更改
0040138C /0F84 F3000000 je Cosh_1.00401485 ; 跳转语句无脑跳转
0040138C /E9 F4000000 jmp Cosh_1.00401485 ; 跳转语句00401391 |90 nopdump下来成一个新文件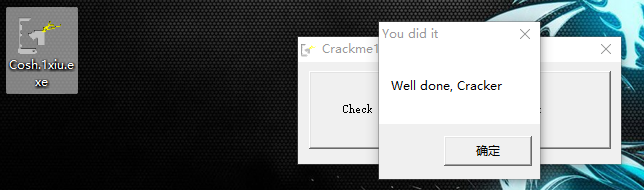
成功.
向上看一下这个CD-Check的过程:
使用Creatflie()函数从C盘符查找到P盘符,看看有没有
CD_CHECK.DAT这个文件,如果有就打开,但是明显我们没有,所以就失败了。
0 0
- 160个CrackMe 027 Cosh.1
- 160个CrackMe 028 Cosh.2
- 160个CrackMe 029 Cosh.3
- 160个练手CrackMe-027
- 160个CrackMe-1-Acid_burn
- 160个CrackMe 002 Afkayas.1
- 160个crackme 004 ajj.1
- 160个CrackMe-第九个
- CRACKME-160-第79个
- 160个CrackMe 077 firework2
- 160个CrackMe之001
- 160个crackme之003
- 160个crackme之004
- 160个crackme之008
- 160个crackme之009
- 160个crackme之010
- 160个crackme之011
- 160个CrackMe之11
- Android Studio详细教程汇总
- 关于C语言字符串和指针的总结
- 二、CSS笔记
- jquery :visible Selector 用于判断元素是否显示
- 自定义Dialog 中setView方法多次调用出错
- 160个CrackMe 027 Cosh.1
- 160个CrackMe 028 Cosh.2
- 160个CrackMe 029 Cosh.3
- Android无需权限显示悬浮窗, 兼谈逆向分析app
- Android Studio常用快捷键、Android Studio快捷键大全
- 笔记-Android Studio配置OpenCV
- iOS-NSURLCache
- windows 8.1 64位PC,Visual Studio 2013 Ultimate,C# .NET 4.0,环境下编写windows服务,亲测成功!
- 一些jquery技巧


